The OWASP Top 10 is a great starting point when learning web application security. HackTheBox offers a track called "The OWASP Top 10," designed to teach these common vulnerabilities through hands-on challenges. In this article, I’ll walk you through the first challenge in the OWASP Top 10 track, called "Looking Glass." solutions.
Whether you’re new to web security or looking to improve your skills, this guide will help you better understand the OWASP Top 10 and how to tackle real-world vulnerabilities.
Let’s Start
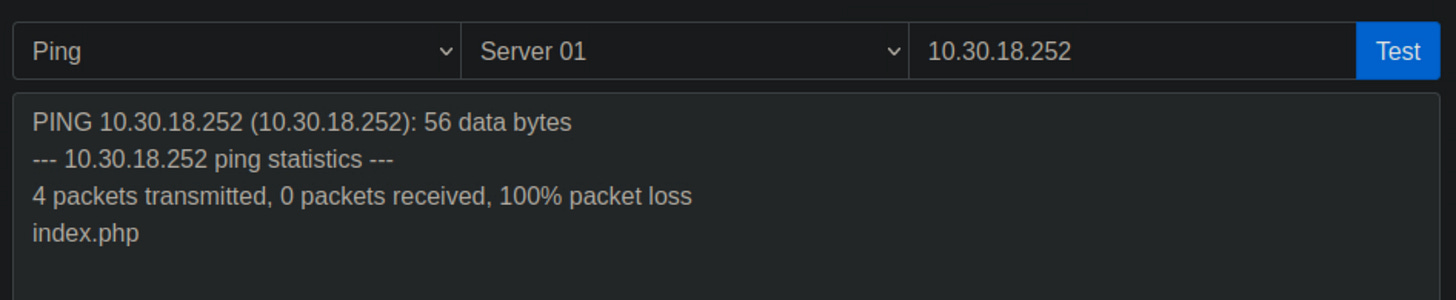
After we deploy the challenge, we are presented with a basic web page that allows users to run ping or traceroute commands against an IP address.
When I tested both commands, I noticed similar output from the command line. This raises suspicions that the web application can execute commands directly.
Here are the parameters while sending the request.
test=ping&ip_address=10.30.18.252&submit=Test
Based on this information, we can try to manipulate the requests from the Burp suite and see how the server responds. First I will try to add a simple ls command to the end. If we run this command we can see something like this.
We can see the files in the current directory. I will try the same in the request.
Don’t forget to encode your requests before sending. You can use decoder tab in Burp. Cyberchef is another alternative to for this.
After we add encoded ls command the request will be look like this:
test=ping&ip_address=10.30.18.252%3b%6c%73&submit=Test
With this request, we can see the files in the current directory.
We now have access to the system. To complete this challenge, we need to create additional requests and find the location of the flag, so we can view its contents.
use the command to list all the files in the / folder:
ls /
test=ping&ip_address=10.30.18.252%3b%6c%73%20%2f&submit=Test
Alright, we found the flag, and its name is flag_rEka9
As the last step, we can run a cat command to see the content of this flag.
cat /flag_rEka9
test=ping&ip_address=10.30.18.252%3b%20%63%61%74%20%2f%66%6c%61%67%5f%72%45%6b%61%39&submit=Test
Got it; we have the flag.