Security teams today juggle AWS misconfigurations, Azure policy drift, Kubernetes posture concerns, GCP access exposure, M365 governance gaps, and the occasional compliance audit that arrives like a surprise tax bill. But instead of duct-taping scripts and dashboards together, there is an open-source tool that already does the heavy lifting:
Prowler – a cloud-native security and compliance platform for AWS, Azure, GCP, Kubernetes, M365, GitHub, MongoDB Atlas, and more.
Prowler is built to help security teams automate assessments, continuously monitor posture, and reduce compliance effort without running agents or deploying complex infrastructure.
What Prowler Does
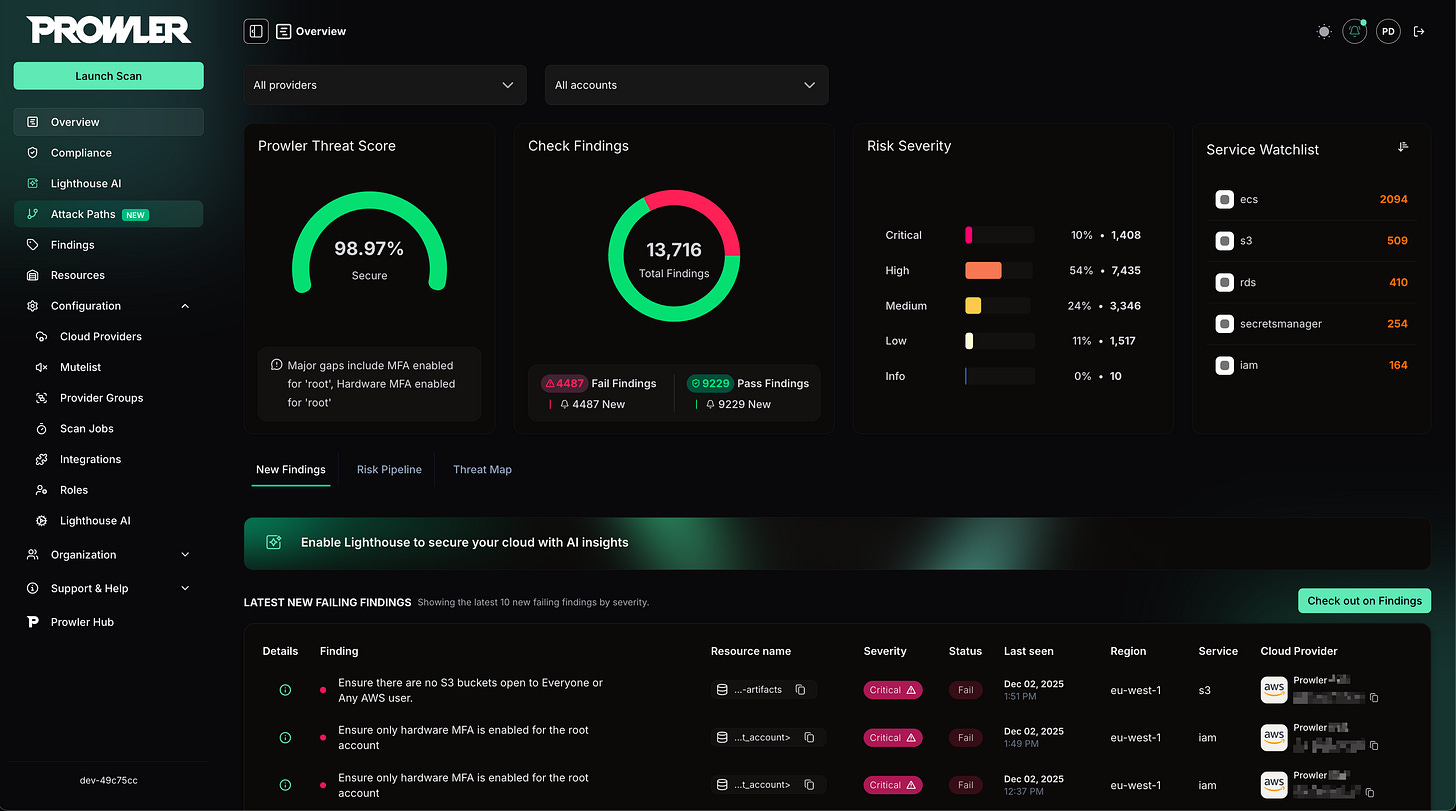
Prowler performs automated cloud environment assessments and maps findings into well-known frameworks. Instead of manually checking IAM rules, public S3 buckets, risky Kubernetes configurations, or forgotten GCP service accounts, Prowler runs hundreds of built-in checks and delivers actionable results.
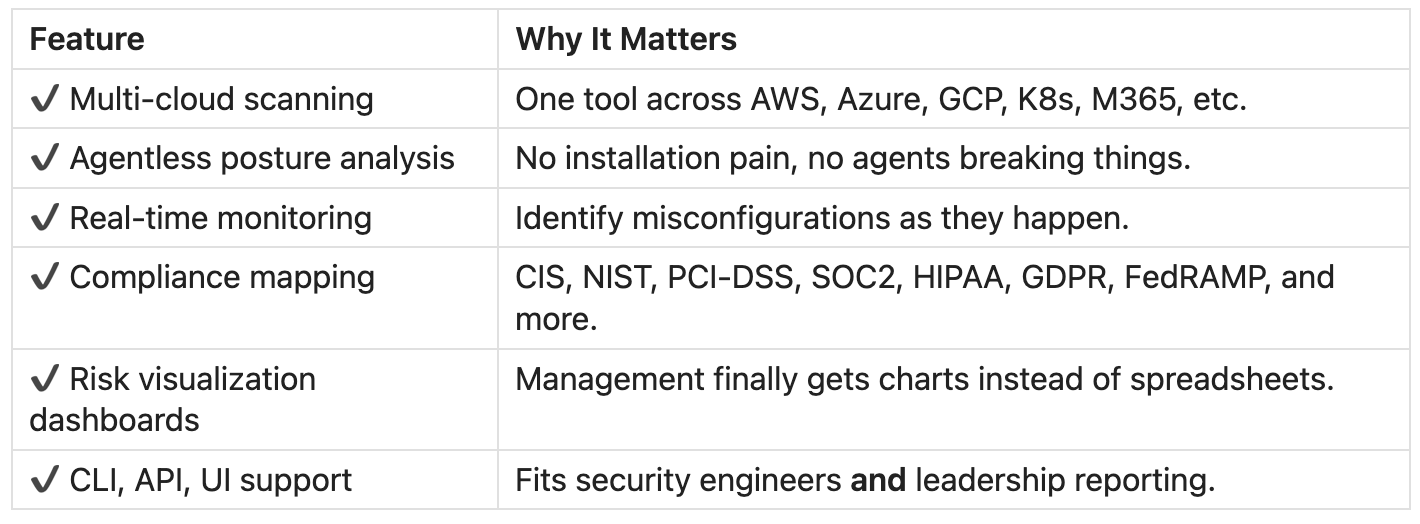
Core Capabilities
The result: less manual work, faster investigations, and faster audit responses.
Why Security Teams Should Care
Security is rarely about a lack of tools. It’s about quickly getting the proper visibility.
With Prowler, teams can:
Detect & Monitor Misconfigurations: Misconfigured buckets, permissive IAM, public assets, weak logging policies — Prowler spots them before an attacker does.
Reduce Audit Burnout: Instead of scrambling during compliance audits, generate framework-mapped reports instantly.
Incident Response Readiness: Better asset visibility means faster containment when things go sideways.
Easy Integration with Existing Workflows: Works in pipelines, CI/CD, Kubernetes jobs, cloud agents, scheduled scans, dashboards, whatever flavor your organization prefers.
Security people love automation. Managers love reduced risk and better metrics. Prowler gives both.
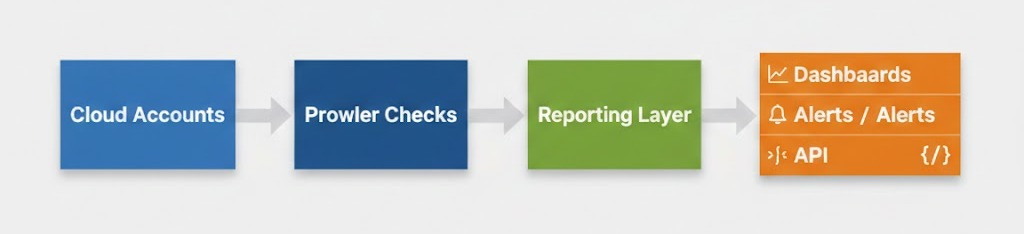
Architecture at a High Level
Even executives can survive this diagram mentally:
Simple. Scalable. You don’t need a PhD in Kubernetes to operate it.
Deployment & Usage
Get started in three ways depending on your environment structure and maturity stage:
Prowler App
UI + backend with scan visualizations, account onboarding, frameworks, and filtering.
Great for SOC, GRC teams, reporting to leadership.
CLI
For engineers running automated scans in CI/CD or schedule-based pipelines.
pip install prowler
prowler aws --list-checks
prowler azure --compliance cis
Containers
When you want clean, repeatable execution across environments.
docker pull prowlercloud/prowler:stable
docker run -it prowlercloud/prowler:stable prowler aws
It scales from one project to a multi-organization cloud with minimal friction.
Who Benefits the Most?
RoleValueSecurity EngineersFast misconfiguration detection & automation.Cloud Ops / DevOpsSafer infrastructure with low friction.Compliance & GovernanceReady-made reporting for audits.Leadership ExecutivesClear picture of security posture.
If your teams spend more time reporting risk than reducing it, Prowler flips that around.
Every company scales cloud services faster than it scales security people. Tools like Prowler give your team the visibility and automation required to defend modern infrastructure without drowning in manual audits.



If you want to do hands on labs I found two options:
- https://www.techwithtyler.dev/academy/my-content-on-pwnedlabs/prowler-and-aws-security-hub
- https://prowler.com/events
But I would recommend using a Docker image for the beginning.
`docker run -it --rm -p 11666:11666 prowlercloud/prowler:stable dashboard`
Is there any learning lab
environment that we can test it?